Check your risk pulse. You don’t WannaCry over risky business.Sponsored
Have you ever wondered if someone else is reading your emails? Have you ever responded to a phishing email? How do you know your staff haven’t done so in your corporate environment? Are you sure a hacker hasn’t already gained access to your corporate information? Does your organisation comply with best practice recommendations and/or regulatory requirements? How do you know?
Risk is inherent in everything we do, especially in business. We all need to take risks to grow and develop our organisations, and, in our fast-paced world, the risks we have to manage are changing and evolving quickly. New cyber threats appear almost daily, disruptive competition is likely around the corner, and it is getting harder to predict future demand for energy.
 We need to proactively manage our business and technical risks so that we can minimise their threat to our organisation and ensure we can continue to grow and thrive. Are you managing your risks to keep your pulse rate down?
We need to proactively manage our business and technical risks so that we can minimise their threat to our organisation and ensure we can continue to grow and thrive. Are you managing your risks to keep your pulse rate down?
Risk management involves understanding, measuring, and mitigating risks that threaten your organisation’s ability to achieve its objectives. A risk is an adverse event that might happen at some point in the future – in 5 minutes, tomorrow or next year. In fact, a risk may never eventuate, however, that doesn’t mean you shouldn’t plan for it, just in case. For example, how often have you had to invoke your business continuity plan? Most organisations never have to invoke it, but they have one because the risk of not having one is too great.
Risks can be contained, impacting only one specific task or activity, or far-reaching, effecting the entire organisation and its
extended networks. For example, remember the WannaCry worm outbreak that was estimated to have infected more than 200,000 computers across 150 countries? This worm brought many organisations to their knees including the UK NHS simply because of a lack of adequate asset management practices – they were running old versions of Microsoft Windows across flat networks so once the malware was inside the trusted networked it spread rapidly. Do you have an adequate asset management and patching policy in place for your organisation? Does your operations team regularly rollout updates to ensure these sorts of risks are being well managed?
Imagine if a hacker infects a smart meter, and perhaps under reports the power consumption, which will impact billing and / or capacity planning or something worse? With the proliferation of smart home devices, smart meters could soon share and exchange information with networked devices, inside and outside our homes, such as air conditioners and cloud-based monitoring software. While this Internet of Things ecosystem is creating new and exciting opportunities for Energy Sector companies, it is also introducing a number of new risks which will need careful management.
Not all risks come from outside the organisation; risks can originate from inside your organisation, too. A careless employee might accidentally share a customer’s personal information or a malicious employee might intentionally share sensitive information outside the network or sabotage your systems. We need to be vigilant to ensure we manage these risks and minimize the potential harm should they eventuate. Remember when the ACC employee accidentally emailed out details of more than 9000 ACC claims? What measures do you have in place to help prevent this sort of data leakage? Do you have an information classification policy to identify the risks to your organisation if certain information is mishandled, and have you put corresponding steps in place to ensure proper handling? What if a staff member is deliberately trying to cause harm? Do you have sufficient controls in place to keep them from succeeding? For example, do you have a segregation of duties policy so no one individual has complete access to every system? Do you have privileged access controls and do you monitor these activities in real-time?
Suppose your organisation wanted to make use of a cloud-based Customer Relationship Management product in which sensitive customer information is to be stored. Without careful consideration of the risks involved in using this cloud-based product, your customer information could be compromised. What would be the resulting impact to your organisation’s reputation?
Risk management does not create risks, it merely helps you recognise and understand the risks you already face. The alternative is to ignore risk until it eventuates, at which point it is generally more critical, expensive and difficult to resolve.
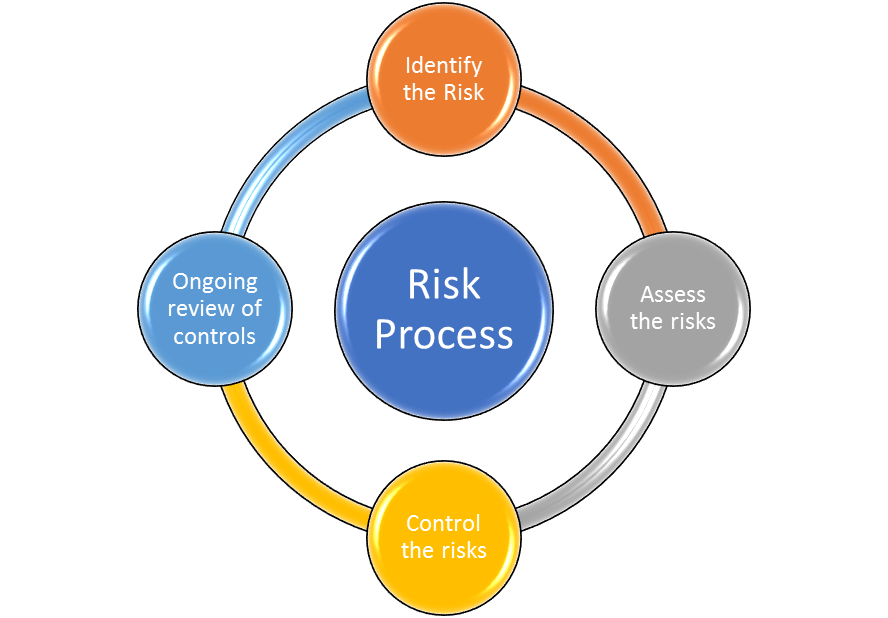
Risk Management is a process of identifying, analysing and assessing risks, developing a plan to control the threats these risks pose to your organisation, and regularly reviewing these controls to ensure they are still relevant and adequately mitigating the risks. Risk management does not stand alone and it needs to be integrated into your business processes.
There are several types of organisational risks to consider in any risk management process:
• Strategic Risk
• Compliance Risk
• Financial Risk
• Operational Risks
• Reputational Risk
• Security Risk
• Other Risks
These different types of risk help to guide the conversation about the risks facing your organisation – what risks do we see that threaten our strategic outcomes? Our ability to comply with regulation? Our ability to stay solvent? And so on.
A wide range of assessment processes are used to identify and quantify a variety of risks, such as;

-
Enterprise Risk Assessment – review and assess your organisational risk management practices, highlighting any significant concerns
-
Project Risk Assessment – identify and measure the risks associated with a particular project, includes reviewing the objectives of the project, the project plan, methodologies, organisational structure, et al.
-
Security Risk Assessment – assess the security risks your organisation currently faces due to existing business policies, practices and technology
-
Solution Risk Assessment – identify and measure the business, security and technical risks associated with a business solution, includes reviewing business processes and application software.
-
Cloud Risk Assessment –assess the business and technical risks associated with moving applications and infrastructure to the cloud, either through migration or subscribing to as-a-Service offerings.
-
Privacy Impact Assessment – identify and measure your organisation’s privacy risks associated with how you collect, use and handle personal information.
-
Gap Analysis - determine the current state of your organisation’s policies, security, human resources and more, and then form a strategy to move into the future.
-
Operational Readiness Review – Prior to production launch or significant change a clear checklist of steps to confirm that documented risks are either mitigated or accepted as low risk.
Any risks identified during one of these assessments must be clearly documented, analysed and prudent mitigations identified and applied. These risks and the agreed mitigations should be reviewed regularly to ensure any changes to the enterprise are considered and the risk remains adequately controlled over time.
Additionally, organisations should train employees in mitigation processes to effectively respond to any risk events that may occur. We can simulate internal and external risk events so our employees are able to respond quickly and efficiently if an event arises.
At the end of the day, the primary goal of any risk management effort is to reduce the adverse impacts on our organisation to an “acceptable level of risk.” This assessment of what is an “acceptable level of risk” is a careful balancing act between the likely impact on the organisation if the risk(s) were to eventuate, and the practical constraints of avoiding the risk(s) – resources, time and cost.
When effective risk management is applied and supported, the benefits far outweigh the effort, and the organisation is set up to succeed.
Click here to check your organisation’s risk pulse.
